Discreet Employee Monitoring on Company PCs: Live Screen View Dashboard & Installation
A purely technical and organisational guide: how a discreet live screen view on company-controlled PCs works in practice – from silent installation to a central dashboard – and why legal admissibility depends on your country, your use case and proper information of users. No legal advice.
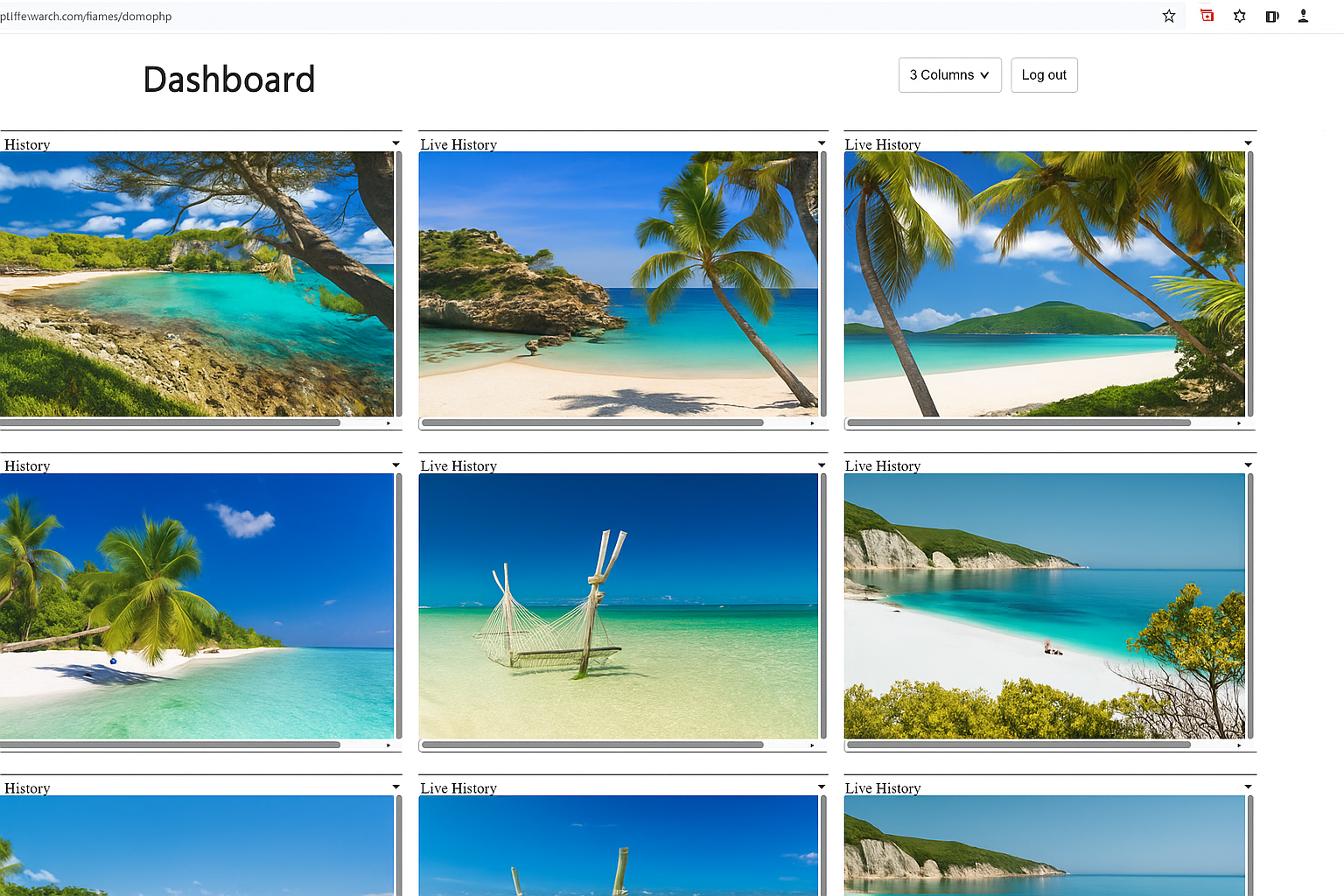
Illustrative Wolfeye dashboard with several company-controlled PCs. Any real-world use of monitoring must comply with applicable laws, contracts and internal policies.
Many owners and IT service providers ask for a way to monitor selected company PCs discreetly – without constant pop-ups, without distracting employees, but with clear technical visibility of what happens on screens during working hours.
Typical questions sound like:
- “Can we monitor employee screens on company PCs without interrupting their work?”
- “Is there a way to run monitoring quietly in the background but still see what happens on key devices?”
- “How can we set up a central live screen dashboard technically – from installation to everyday viewing?”
At the same time, “discreet” must never be confused with “without rules”. Whether you may use any monitoring software, in which way (for example, for training supervision, quality assurance or security) and under which conditions (for example, information duties, consent, contractual clauses) depends on the laws and regulations in each relevant country, on your industry and on your specific setup.
This article does not provide legal advice. It only describes technical possibilities and typical organisational patterns for discreet live screen monitoring on company-controlled PCs and explicitly does not say what is legally allowed in any particular country or situation.
Before you deploy Wolfeye or any other monitoring software, always obtain individual legal advice in all relevant jurisdictions – especially about:
- whether and under which conditions you may monitor company PCs used by employees, remote workers or freelancers,
- whether prior information, explicit consent or specific contractual clauses are required,
- and how data protection, employment law and client contracts interact in your case.
1. What “Discreet” Technically Means in Employee Screen Monitoring
When we talk about “discreet employee monitoring” in a technical context, we usually mean:
- The monitoring software runs in the background on company-controlled Windows PCs.
- There are no constant pop-ups, alerts or dialogs that interrupt employees’ work.
- Authorised persons can see live screen contents and – depending on configuration – a screenshot history in a central dashboard.
- The tool does not require employees to actively start or confirm the software each day.
From a technical perspective, Wolfeye Remote Screen follows a clear model:
- You install a small agent on each company PC you want to monitor.
- The agent sends screen contents to your Wolfeye account via the internet.
- In the live dashboard, authorised users see single screens or a grid of multiple PCs.
Whether this kind of discreet setup is legally admissible in your country and for your specific use case (for example, training supervision, quality assurance or security) – and whether you must inform employees or obtain consent – is always a legal question and must be clarified separately with qualified legal counsel.

Example: live screen dashboard in Wolfeye Remote Screen with several company-controlled PCs. Image for technical illustration only. Any real-world use of monitoring must comply with applicable laws, contracts and internal policies in all relevant countries.
2. Technical Basics: Company-Controlled PCs, Not Private Devices
In almost all practical scenarios, discreet monitoring focuses on company-controlled PCs, for example:
- Office desktops and laptops owned by the company,
- company laptops used in home offices or co-working spaces,
- PCs in training rooms or shared workstations,
- devices at external service providers that are technically and contractually under your control.
Typical technical characteristics of such setups:
- Central installation and updates: the Wolfeye agent can be rolled out centrally (for example via remote software or group policies) on selected company PCs.
- Defined target group: you usually start with a limited group of devices, for example “support team PCs”, “training PCs” or “PCs used by new hires”.
- Network independence: monitoring works as long as the PCs have internet access – no complex VPN or remote desktop infrastructure is required.
Whether and under which conditions you may install monitoring software on private devices (for example, freelancers’ personal laptops) is legally much more sensitive and is not covered by this article. Always clarify such cases first with legal experts before considering them technically.
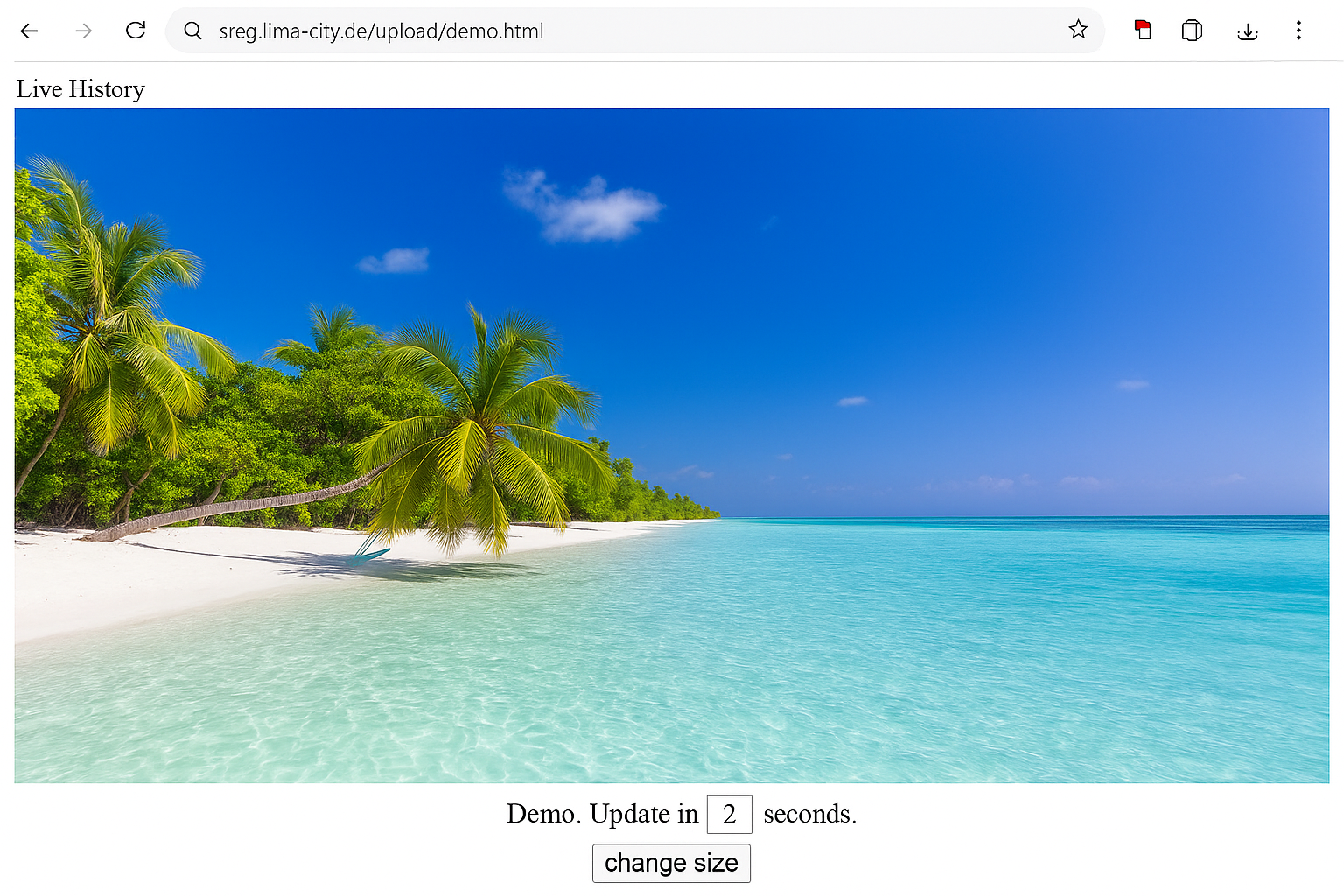
Example: live view of a single company-controlled PC. It shows what is technically possible; it does not say anything about what is legally allowed. Always obtain legal advice before monitoring employee PCs.
3. Step-by-Step: Silent Installation on Company PCs (Technical View Only)
The video “Discreet Employee Monitoring Live Screen View on Company PCs Without Interrupting Work – INSTALLATION” shows a technical demo of how a silent rollout can look on company-controlled PCs.
From a purely technical perspective, the process can be summarised in a few typical steps (details may vary depending on your infrastructure):
- Create your Wolfeye account and log into the dashboard.
- Download the installer for company PCs from your account area.
- Roll out the agent:
- via manual installation on a few PCs (for small tests), or
- via remote software, group policies or your RMM tool for larger environments.
- Verify connectivity in the dashboard: newly installed PCs should appear in your list or in the grid shortly after installation.
- Group PCs logically, for example by location (“Office A”), team (“Support”) or use case (“Training PCs”).
Important: this is only a technical description. Before you install any monitoring software, always clarify with legal counsel:
- whether you may install the agent at all on the selected PCs,
- whether you must inform staff, obtain consent or adjust employment and service contracts,
- and how you should document usage and access rights internally.
4. Step-by-Step: Using the Live Screen Dashboard Without Interrupting Work
The dashboard video “Discreet Employee Monitoring Live Screen View on Company PCs Without Interrupting Work – DASHBOARD” focuses on everyday usage: how you actually work with a live screen view once the agent is installed on selected company PCs.
Typical patterns include:
4.1 Short overview checks instead of permanent viewing
Most organisations do not watch employees all day. Instead, they introduce short overview routines:
- a brief grid overview at the start of a shift,
- spot checks during critical times (for example, when queues are long or quality issues appear),
- targeted checks when specific questions or incidents occur.
4.2 Supporting training, coaching and process changes
In many cases, the live view is used to support training or onboarding on company PCs:
- Trainers can see where users struggle in new systems,
- coaches can verify whether new process steps are actually followed on screen,
- and concrete guidance becomes easier when you see the same interface as the employee.
Again, whether and how such usage is legally allowed in your country depends on local laws and must always be clarified individually.
4.3 Clear access rules and roles
In a discreet monitoring setup, it is important that only a few authorised people can see the live screens. Technically, this can mean:
- Limiting dashboard access to owners, team leads or specific IT staff,
- using role-based access control where available,
- and documenting who has access and for which purpose (for example, training supervision, quality assurance, security).
5. Best Practices for Discreet Monitoring on Company PCs (Non-Legal, Organisational View)
Besides technical setup, many organisations adopt a few basic best practices for discreet monitoring on company-controlled PCs – in addition to obtaining legal advice:
- Company devices only: clearly separate company PCs from private devices. Monitoring private hardware is often highly sensitive or inadmissible.
- Defined use cases: document why you use live monitoring at all (for example, training supervision, quality assurance, security) and which PCs are included.
- Limited retention: if you use screenshot history, define together with legal and data protection experts how long you store screenshots and when they are deleted.
- Transparent internal processes: where laws or contracts require it, inform affected users appropriately and document this information process.
- Regular reviews: review on a regular basis which PCs are monitored, who has access and whether the defined purposes are still valid.
These points are not legal advice. They are only meant to help you structure internal discussions between IT, HR, management and legal teams.
6. Video: Discreet Installation on Company PCs (Technical Demo)
The following video shows a purely technical demo of how to install Wolfeye Remote Screen on company-controlled PCs for discreet live monitoring.
Important: the video does not state what is legally allowed in your country. It does not replace legal advice.
Video: “Discreet Employee Monitoring Live Screen View on Company PCs Without Interrupting Work – INSTALLATION”. The video shows what is technically possible on company-controlled PCs and does not make any statement about legal admissibility.
7. Video: Live Screen View Dashboard Without Interrupting Work (Technical Demo)
This video shows the live dashboard of Wolfeye Remote Screen in action and how you can see multiple company PCs in one overview without interrupting employees’ work.
Again, this is a technical demo only and no legal advice. It does not guarantee that any specific use of monitoring is lawful in your country or industry.
Video: “Discreet Employee Monitoring Live Screen View on Company PCs Without Interrupting Work – DASHBOARD”. It illustrates how a live screen dashboard works technically and does not replace individual legal advice.
Frequently Asked Questions – Discreet Monitoring on Company PCs
No. Using company-controlled PCs is an important technical precondition, but legal admissibility also depends on applicable laws, the concrete purpose of monitoring (for example, training supervision, quality assurance, security) and whether information, consent or contractual clauses are required. Always clarify this with legal counsel.
This article does not answer that question. Whether you must inform employees or obtain consent is a legal question that depends on your country and your specific scenario. In many jurisdictions, transparency and clear information duties are essential. Always obtain legal advice before deploying any monitoring software.
Technically, Wolfeye can run unobtrusively in the background on company PCs. Whether and how you design communication around this (for example, policies, onboarding information, consent forms) is a strategic and legal decision that must be taken together with HR, legal and data protection experts.
No. Wolfeye provides visual insight into screen activity (live view and, depending on configuration, screenshot history). It does not replace contractual arrangements, time tracking, HR systems or data protection management.
Conclusion
Discreet employee monitoring on company PCs is first and foremost a technical possibility – never an automatic permission.
From a technical and organisational perspective, tools like Wolfeye Remote Screen can help you:
- see selected company-controlled PCs in a live screen dashboard without interrupting work,
- support training, coaching and process changes more effectively,
- and understand quality and workflows better across teams and locations.
A pragmatic approach can be:
- first define your intended use cases and device groups (for example, “training PCs in country A”, “support team PCs in location B”),
- then discuss them with legal counsel, HR and data protection experts in all relevant jurisdictions,
- and only then roll out a focused pilot on clearly defined, company-controlled devices – within the limits set by law and your own internal policies.
Want to see how a discreet live screen dashboard could look on your own company PCs?
Start 14-Day Free Trial
Wolfeye is monitoring software for company-controlled PCs. Any use must comply with the laws and regulations that apply in all relevant countries, your industry and your specific use case (for example, training supervision, quality assurance or security). In many jurisdictions, the admissibility of discreet monitoring depends on factors such as prior information of users, explicit consent, data protection rules and contractual terms. This article and the embedded videos are for general technical and organisational information only and do not constitute legal advice or a guarantee of legal admissibility.
Before using any monitoring software such as Wolfeye, always obtain independent legal advice in all relevant countries about whether and how you may monitor company-controlled PCs (for example in training, quality assurance or security scenarios) and under which conditions users must be informed or give consent.