IT Service Providers & MSPs: How to Offer Live Screen Monitoring as a Managed Service with Wolfeye
A non-legal, technical and organisational guide for IT service providers and MSPs: how to structure multi-client deployments of Wolfeye Remote Screen, position live screen monitoring as a managed service and stay aware of legal boundaries in your country and use cases.
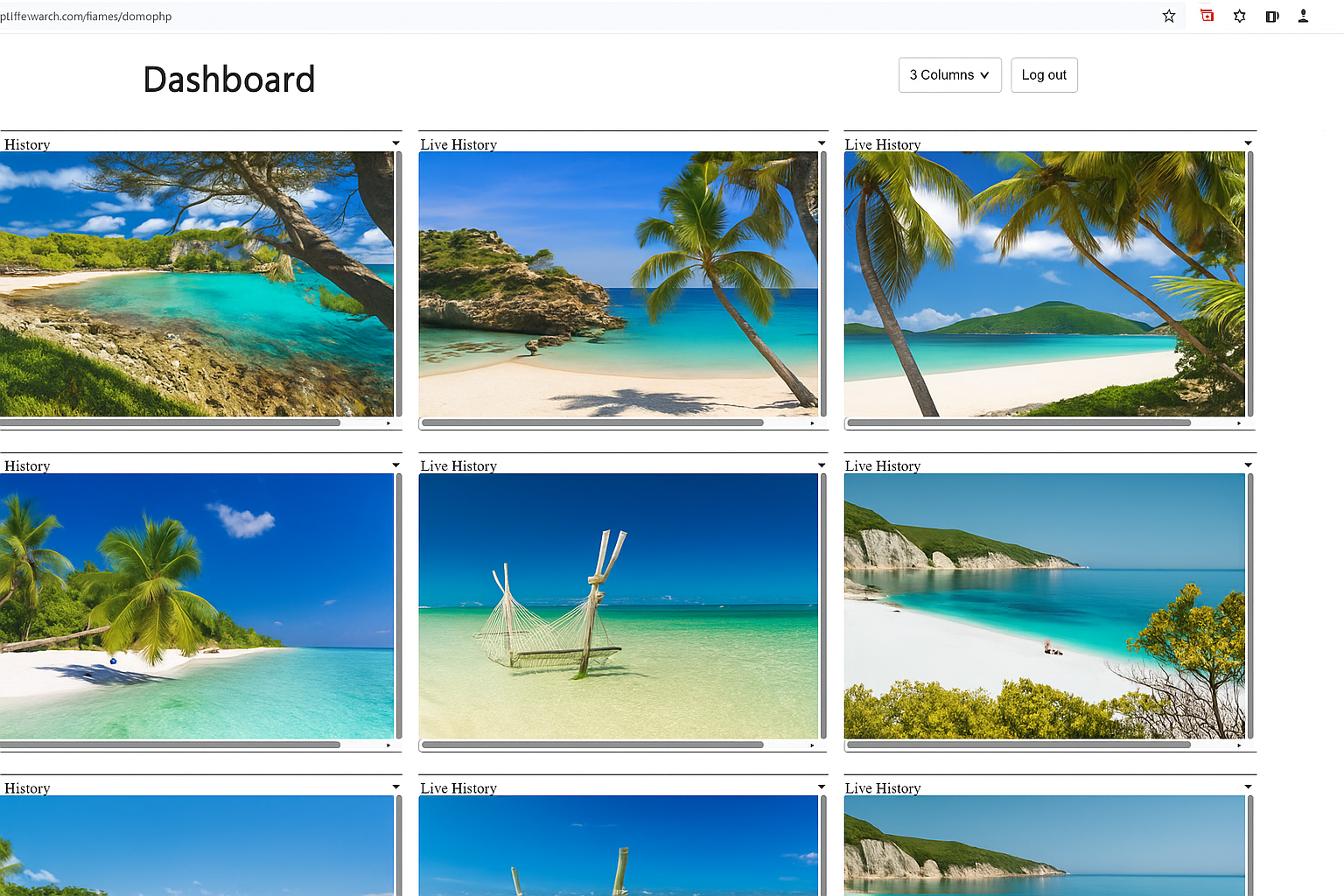
Illustrative Wolfeye dashboard in an MSP scenario: several company-controlled client PCs side by side. Image for technical illustration only; any real use of monitoring must comply with applicable laws and regulations.
For many IT service providers and managed service providers (MSPs), Wolfeye Remote Screen is interesting for a very specific reason:
“Can we offer live screen monitoring of company-controlled PCs as a managed service for our clients – and how would that work technically?”
From a technical and organisational perspective, the answer is: yes, you can build recurring services around live screen and screenshot visibility on selected client PCs. Typical examples are training PCs, support workstations, call centre agents or other clearly company-controlled devices.
At the same time, screen and employee monitoring is always a legally sensitive topic. Whether you or your clients may use software like Wolfeye at all, for which purposes (for example, training supervision, quality assurance or security) and under which conditions (for example, prior information of employees, explicit consent, internal agreements) depends on the legal framework in the respective country and on the specific use case.
This article therefore focuses strictly on technical possibilities and organisational patterns for IT providers and MSPs. It does not make any statement about what is legally permitted in any country and it is not legal advice.
Before you or your clients deploy Wolfeye or any other monitoring software, you should always obtain individual legal advice in the relevant jurisdiction. Legal experts can help clarify in particular:
- whether and under which conditions monitoring of company-controlled PCs is allowed at all,
- for which specific use cases (for example, supervision of training sessions or quality checks) monitoring may be permissible,
- whether employees or users must be informed in advance or give explicit consent,
- how responsibilities are allocated between the client organisation and the IT provider.
1. What Role Can Live Screen Monitoring Play in an MSP Service Portfolio?
From a business and organisational point of view, live screen monitoring with Wolfeye can be a building block in a broader managed service offering for your clients. Typical scenarios include:
- Training and onboarding support: your client uses company-controlled training PCs, and you provide the technical basis so supervisors can see in real time how trainees work through processes.
- Process and quality transparency: key support or back office PCs are visible in a live dashboard so that team leads can better understand everyday workflows.
- Hybrid and remote setups: selected office and remote PCs of a client are visible in one dashboard, giving management a clearer technical view of daily operations.
- Troubleshooting support: during support calls, authorised staff can see what happens on important company PCs to resolve issues faster.
In many cases, managed service providers design monitoring as an add-on service on top of existing contracts – for example, as a “screen visibility package” billed per monitored company PC or per client site.
Which of these scenarios are legally permissible and under which conditions depends on national law and must be clarified with legal counsel by you and your clients.
2. Technical Multi-Client Setup: How IT Providers Typically Structure Wolfeye
From a purely technical perspective, a multi-client setup for IT providers and MSPs with Wolfeye often follows patterns such as:
- Separate environments per client: each client organisation uses its own Wolfeye environment or account, so that screens and PCs are clearly separated.
- Company-controlled Windows PCs only: Wolfeye is installed on selected, clearly company-controlled PCs of the client (for example, office workstations, training PCs, company laptops).
- Groups per team or use case: within a client, monitored PCs can be grouped logically (for example, “Support”, “Training PCs”, “Back office”).
- Role-based access: the client’s authorised managers and supervisors receive access to specific groups; the IT provider gets technical admin access only where contractually agreed.
A technically typical rollout from the IT provider perspective might look like this (again, assuming legal questions have been clarified beforehand):
- Clarify scope and client use cases
Together with the client, you define which company-controlled PCs should be visible (for example, 10 support PCs and 5 training PCs) and for what purposes (for example, training supervision, process transparency). - Prepare the client’s Wolfeye environment
You set up or configure the client’s Wolfeye environment, including technical settings and basic groups. - Install Wolfeye on selected company PCs
Using your usual tools (for example, RMM, software deployment, group policies), you roll out the Wolfeye software to the agreed client PCs. - Name and group PCs clearly
In the dashboard, you assign clear names to each PC (for example, “ClientA-Support-01”, “ClientA-Training-03”) and organise them into groups. - Provide access for authorised client staff
You set up accounts or access permissions so that only designated persons at the client can see the live screens relevant to them.
Important: how exactly you may access client environments yourself and what you are allowed to see is not just a technical question but one of contracts and law. Always clarify access rights and responsibilities contractually and with legal advice.

Example: a Wolfeye dashboard with multiple company-controlled PCs arranged in groups. The image is for technical illustration only. Any real use of monitoring must comply with the laws and regulations that apply in the client’s country, industry and specific use case.
3. Packaging Live Screen Monitoring as a Managed Service (Business View, Not Legal Advice)
From a business perspective, many IT providers and MSPs think in terms of service packages. Technically, Wolfeye can fit into such packages in several ways, for example:
- Per-PC add-on: the client pays a monthly fee per monitored company PC, on top of existing managed service bundles.
- Per-team package: a fixed monthly package for a certain number of monitored support, call centre or back office PCs.
- Training & onboarding package: a dedicated offer where you provide the technical basis for supervising training PCs – for example, for new staff during their first weeks.
In all of these models, live screen monitoring is only one component among others (for example, endpoint management, backups, security). It is important that your contracts clearly describe:
- which PCs are included and under which conditions they may be monitored,
- who is responsible for informing employees or obtaining consent where required by law,
- and which purposes are covered by the service (for example, training supervision, quality checks, support).
This article cannot provide legal wording or contract templates. It simply shows how Wolfeye can be used technically in such service models once legal questions have been clarified.
4. Example Scenarios for IT Service Providers and MSPs
From a technical and organisational standpoint, IT providers often integrate Wolfeye into recurring client scenarios. A few examples:
4.1 Support & helpdesk teams at a client
You deploy Wolfeye on selected support PCs of a client. Supervisors can see live screens during peak times and understand how tickets are processed in practice. You are responsible for the technical operation; the client is responsible for legal and HR matters.
4.2 Training PCs for new hires
The client runs regular onboarding sessions on training PCs. With Wolfeye, trainers can see in real time how new staff follow the steps in CRM, ERP or ticket systems. Whether and how they must inform participants and document this is a legal question that the client must clarify with legal counsel.
4.3 Multi-location client with hybrid teams
A client runs several small branches and has staff working from home. You deploy Wolfeye on a selection of company laptops and office PCs so that management can view a cross-section of daily activity. Technically, this is straightforward – but the legal admissibility depends entirely on the laws and internal rules that apply to the client.
In all of these cases, Wolfeye is a technical tool. It does not decide what is allowed. Your role as an IT provider is to offer a technically clean implementation once legal and organisational questions have been settled on the client side.
5. Privacy by Design for MSPs: Limiting Scope, Access and Retention
Because monitoring is sensitive, many IT providers decide together with their clients to implement privacy by design principles at the technical level. For example:
- Minimal necessary scope: installing Wolfeye only on those company PCs that are absolutely necessary for the agreed purpose (for example, training PCs or selected support PCs).
- Limited access: restricting visibility to a small group of authorised client managers instead of broadly accessible dashboards.
- Clear time limitations: using live screen monitoring, for example, only during training periods or business hours, not around the clock.
- Transparent configuration: documenting which PCs are monitored, for which purposes and with which technical settings.
Technically, Wolfeye provides enough flexibility to implement such limitations. How exactly they should be set up in each client organisation should always be defined together with legal, HR and data protection experts on the client side.
6. Legal Considerations and Explicit Disclaimer for IT Providers
Because IT providers and MSPs often work across multiple clients and jurisdictions, the legal dimension is particularly important. For that reason, this article ends with a clear disclaimer:
This article describes technical possibilities and typical organisational patterns of using Wolfeye Remote Screen in IT service provider and MSP scenarios. It is not legal advice and does not state what is permitted in any specific country or situation.
In many jurisdictions, aspects such as the following may be relevant for the legal admissibility of monitoring (examples only):
- Which laws and regulations apply in the client’s country and industry (for example, data protection and employment law).
- Whether only company-controlled devices are monitored or also private devices (which may be heavily restricted or prohibited).
- For which purposes monitoring is used (for example, training supervision, quality assurance, security) and whether those purposes are proportionate.
- Whether employees or users must be informed in advance and whether explicit consent is required in certain scenarios.
- Whether works councils or similar bodies must be involved and which internal agreements are required.
Before you include live screen monitoring in any managed service offering, you and your clients should always obtain individual legal advice in the relevant jurisdiction. Only qualified legal experts can tell you:
- whether and under which conditions monitoring of client PCs is permissible,
- how employees or users must be informed and whether consent is required,
- and how responsibilities between the client and the IT provider should be allocated contractually.
Always treat Wolfeye as a technical component that you may only deploy within the limits of applicable law and your clients’ internal rules – never as a substitute for legal or HR decisions.
7. Video Walkthrough: Wolfeye for IT Service Providers & MSPs
The following video shows a technical walkthrough of how Wolfeye Remote Screen can be used from the perspective of IT service providers and MSPs, for example to manage multiple client environments and monitor selected company-controlled PCs.
The video is a technical demo for professionals and does not replace legal advice. It does not guarantee that any specific use is lawful in your country or in your clients’ situations.
Video: technical demo of Wolfeye Remote Screen for IT service providers and MSPs. The video illustrates technical possibilities only. It does not make any statement about what is legally allowed in any specific country, industry or client use case.
Frequently Asked Questions – IT Providers & MSPs Using Wolfeye
From a technical perspective, yes: many IT providers structure separate Wolfeye environments or accounts per client and then install the software only on selected company-controlled PCs at each client. How these environments are organised and who may access what must always be defined contractually and in compliance with applicable law.
Technically, you can provide the infrastructure so that your client’s trainers or supervisors see how trainees work on company PCs. Whether and under which conditions training supervision via screen monitoring is allowed in a given country depends on local law, information duties and consent requirements. Always ask legal experts before offering such a service.
No. Wolfeye focuses on live screen view and screenshot history on company PCs. It does not replace classical RMM or remote access solutions. Many IT providers simply add Wolfeye as a dedicated “screen visibility” layer on top of their existing toolset.
Legal responsibilities depend on contracts, roles and the laws in the relevant jurisdiction. This article cannot answer that question. In practice, it is essential that you and your clients clarify with legal counsel who is responsible for which information duties, consents and internal agreements before monitoring is deployed.
Conclusion
For IT service providers and MSPs, Wolfeye Remote Screen can be a technical building block for managed services around live screen visibility on selected company PCs.
From a purely technical and organisational perspective, it can help you:
- provide your clients with more transparency on how processes run on key workstations,
- support training and onboarding on company-controlled PCs,
- and structure recurring service packages around clearly defined groups of monitored devices.
A pragmatic approach for IT providers and MSPs is therefore:
- first define concrete, limited use cases together with the client (for example, “10 support PCs”, “5 training PCs”),
- then clarify legal and contractual questions with qualified legal experts,
- and only then roll out a technically clean pilot on clearly defined, company-controlled client PCs.
Want to explore Wolfeye for your MSP or IT service business?
Start 14-Day Free Trial
Wolfeye is monitoring software. Any use must comply with the laws and regulations that apply in the relevant country, industry and specific use case (for example, training supervision, quality assurance or security purposes). In many jurisdictions, the admissibility of monitoring depends on factors such as prior information of employees, explicit consent or further formal requirements. This article and the embedded video are for general technical and organisational information only and do not constitute legal advice or a guarantee of legal admissibility.
Before using any monitoring software such as Wolfeye, always obtain independent legal advice in the relevant country about whether and how you and your clients may monitor company-controlled PCs (for example in training supervision, quality assurance or security contexts) and under which conditions employees or users must be informed or give consent.