IT Security + Productivity for SMBs – With Real Screen Data Instead of Guesswork
How IT providers use Wolfeye to make cyber risks and time-wasting in remote work visible. With example scenario, model numbers and a 14-day rollout plan (not legal advice).
An SMB with 12 remote employees repeatedly encounters suspicious emails and slow response times in support.
One employee regularly spends time on obviously risky websites – right in the middle of the workday.
The IT provider decides to add monitoring software such as Wolfeye on top of existing security tools.
In an internal example evaluation, the company estimates around 35% fewer clearly risky websites and about 30% more productive time over several weeks – with the same team size.
Important: These are model numbers from a case-style example, not a general promise.
Whether and how you may use monitoring for your clients (employee information, consent, works council, internal policies, etc.) depends entirely on applicable labour and data protection laws.
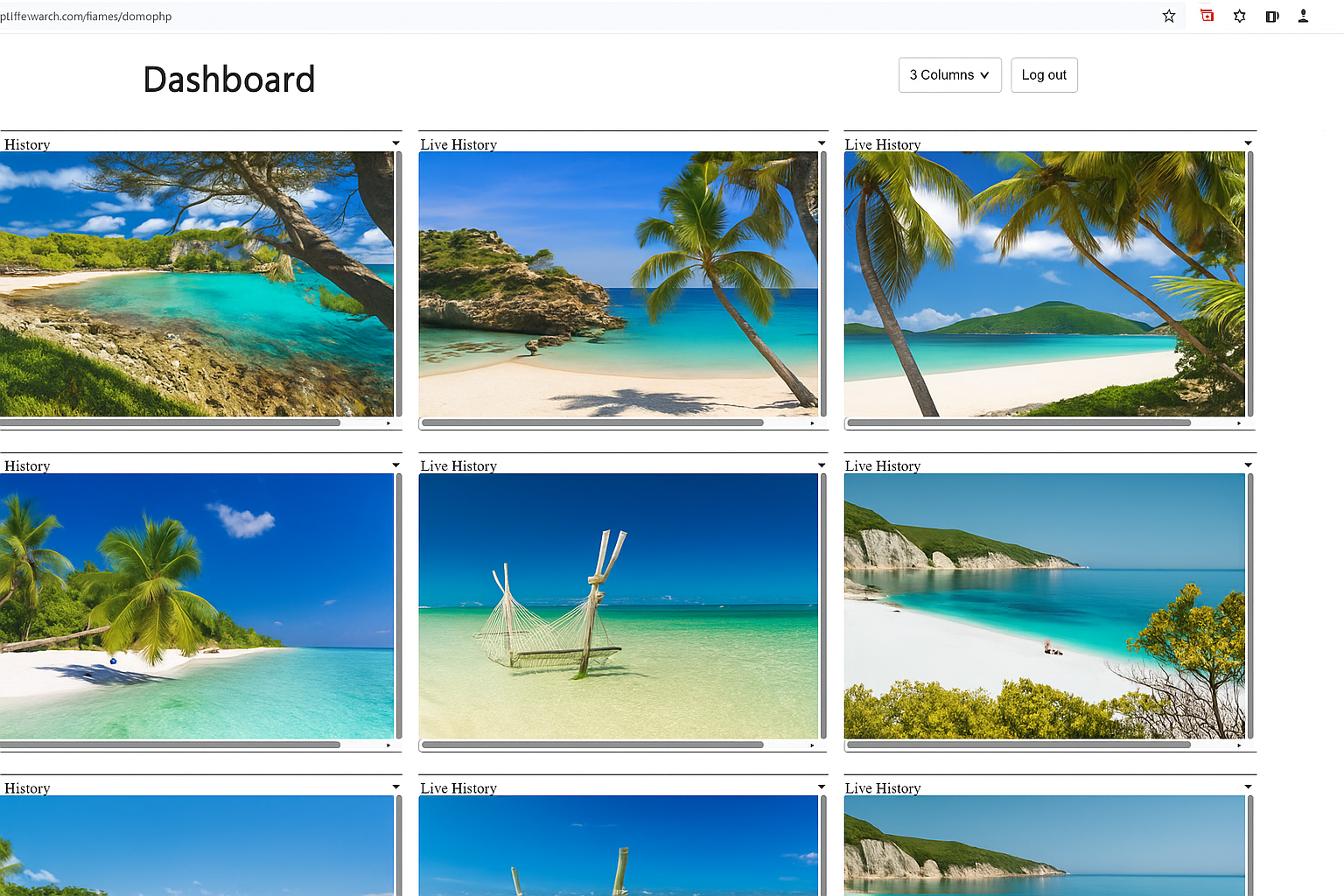
Foto: Pexels (CC0) – Remote-Team & Sicherheit (Symbolbild)
The Double Challenge: Cyber Risks + Time Waste
Many SMBs, especially with remote or hybrid teams, face a double challenge:
1. Cyber risks: Various reports highlight that small and mid-sized companies are frequent targets for phishing, ransomware and social engineering.
A single careless click on a manipulated website or file can cause serious damage.
2. Productivity loss: In many surveys and studies, businesses report that a noticeable share of working time flows into private browsing, social media or news sites – particularly in home office setups.
The exact percentage varies widely by industry, culture and leadership style.
The common root cause: limited transparency about what actually happens during working hours, both from a security and productivity perspective.
Wolfeye: Background Monitoring as an Additional Security and Decision Layer
Wolfeye is monitoring software that can be configured to run in the background without interfering with day-to-day work.
On the server, screenshots from client PCs are updated at short intervals (for example every few seconds, depending on configuration).
In the default mode, only the current screenshot is kept – each new image overwrites the previous one.
As long as the screenshot history feature is disabled, this does not create a permanent screenshot archive.
You can optionally enable a screenshot history, in which case screenshots are stored permanently in a history folder at defined intervals.
Details on intervals, storage location and access rights should be documented in your privacy policy and internal guidelines.
Using these data, your client can, for example, identify:
- regular access to obviously risky websites,
- an unusual amount of time spent on private activities,
- and how focus phases and distractions are distributed throughout the day.
Example: Logistics SMB with 12 PCs – Less Risk, More Output (Model Calculation)
A logistics SMB with 12 Windows PCs already uses antivirus, firewalls and email filters. However, suspicious links and attachments keep appearing.
The IT provider deploys Wolfeye (after clarifying privacy and internal rules).
Over the first few days, clear patterns appear in the dashboard:
- two employees repeatedly visit websites that look highly questionable,
- several hours per week go into social media, video platforms and private communication,
- long idle periods occur between ticket changes.
- targeted phishing and download awareness training,
- defined focus times where private browsing is off limits,
- simple KPIs (tickets per day, response times).
- clearly risky web activity has dropped significantly,
- productive hours have increased noticeably,
- and potentially costly incidents may have been avoided.
Your Advantage as an IT Provider
1. Dual value: You support both cybersecurity and efficiency in remote teams at the same time.
2. Recurring revenue: Licensing, setup, ongoing support and optional reporting.
3. Strategic positioning: Instead of “We just keep systems running”, you can say:
“We help you reduce risk and improve remote productivity based on real data.”
4. Complement, not replacement: Wolfeye adds visibility on top of antivirus, EDR, firewalls and MDM – it does not replace them.

Foto: Unsplash (CC0) – Monitoring-Dashboard (Symbolbild)
Why Discreet Monitoring Often Works Well for SMBs
Highly visible, heavy-handed monitoring often leads to resistance, workarounds and mistrust.
Many real-world stories show that employees quickly adapt their behaviour only temporarily when they feel constantly watched.
A carefully framed, discreet monitoring approach – embedded in transparent rules, clear goals and a solid legal foundation – can instead:
- deliver realistic data over longer periods,
- enable targeted measures such as training or process optimisation,
- and reduce arguments about “perceived productivity”.
Your 14-Day Plan: Introduce Wolfeye in a Legally Sound Way (Example, Not Legal Advice)
- Day 1: Check whether Wolfeye fits the client’s infrastructure (Windows, server, connectivity). Get an initial legal view (data protection officer, lawyer, works council as applicable).
- Day 2–4: Install Wolfeye on selected PCs (about 5 minutes per PC) and, within the legal framework, start collecting data without publicly blaming individuals.
- Day 5: Together with the client, identify the most obvious risky sites and time-wasters. Focus on patterns, not on “naming and shaming”.
- Day 6: Derive technical measures (e.g. blocking specific domains with DNS filters, updating security policies).
- Day 7: Define focus times and simple rules (e.g. no private websites during 9–11 am).
- Day 8: Run a short security and awareness training (e.g. 15 minutes via Teams/Zoom).
- Day 9–12: Monitor how things develop: fewer risky sites, more tickets closed, more stable response times.
- Day 13: Prepare a before/after overview (qualitative plus rough metrics – as an example, not a binding promise).
- Day 14: If results are positive, formalise Wolfeye usage and monitoring rules in policies or agreements.
Sample Before/After Values (Model Numbers)
Note: The figures below are sample values from a model scenario – not a guarantee for specific results.
| Metric | Before (Example) | After ~30 Days (Example) | Trend |
|---|---|---|---|
| Visits to clearly risky sites per day | 18 | 5 | strong decrease |
| Productive hours per week | 24 | 33 | noticeable increase |
| Obvious time waste | 16 hrs | 7 hrs | strong decrease |
Frequently Asked Questions
Wolfeye is technically designed to run in the background and not stand out during normal use. However, whether and how your clients must inform employees or obtain consent is solely determined by the applicable labour and data protection laws and any internal agreements.
If Wolfeye is active and the affected PC is connected, an authorised person can see the screen at short intervals and react more quickly. Still, technical protections such as antivirus, EDR and email filtering remain essential.
No. Wolfeye complements existing tools (e.g. firewalls, antivirus, MFA, EDR) and does not replace them. It adds visibility to help identify patterns and risks.
In default mode, only the current screenshot is kept on the server; each new image overwrites the previous one. This means no permanent screenshot archive is created as long as the history feature is disabled.
When screenshot history is enabled, images are stored at defined intervals. Details on storage, retention and access should be described in your privacy policy.
Licensing starts at around $80 per PC per year. View current pricing →
Yes – Wolfeye can be tested free of charge for 14 days, which is ideal for a small pilot. Start demo →
Conclusion
IT security and productivity do not have to compete – they can reinforce each other.
With monitoring software like Wolfeye, you as an IT provider gain additional transparency into risky websites, critical patterns and obvious time-wasters –
always assuming that the deployment is legally sound and properly communicated.
The percentage improvements mentioned in this article are model calculations.
How much risks and productivity actually change for your clients depends on many factors (starting point, culture, processes, legal framework).
If you want to see what Wolfeye looks like in a real remote or hybrid environment, the best next step is a 14-day pilot with a selected client.