Time Theft & Timesheet Fraud: How to Verify Actual Work with Live Screen View
A practical, non-legal guide for SMBs, agencies and IT service providers: how live screen view plus screenshot history can support timesheet verification on company-controlled PCs — only where legally permitted.
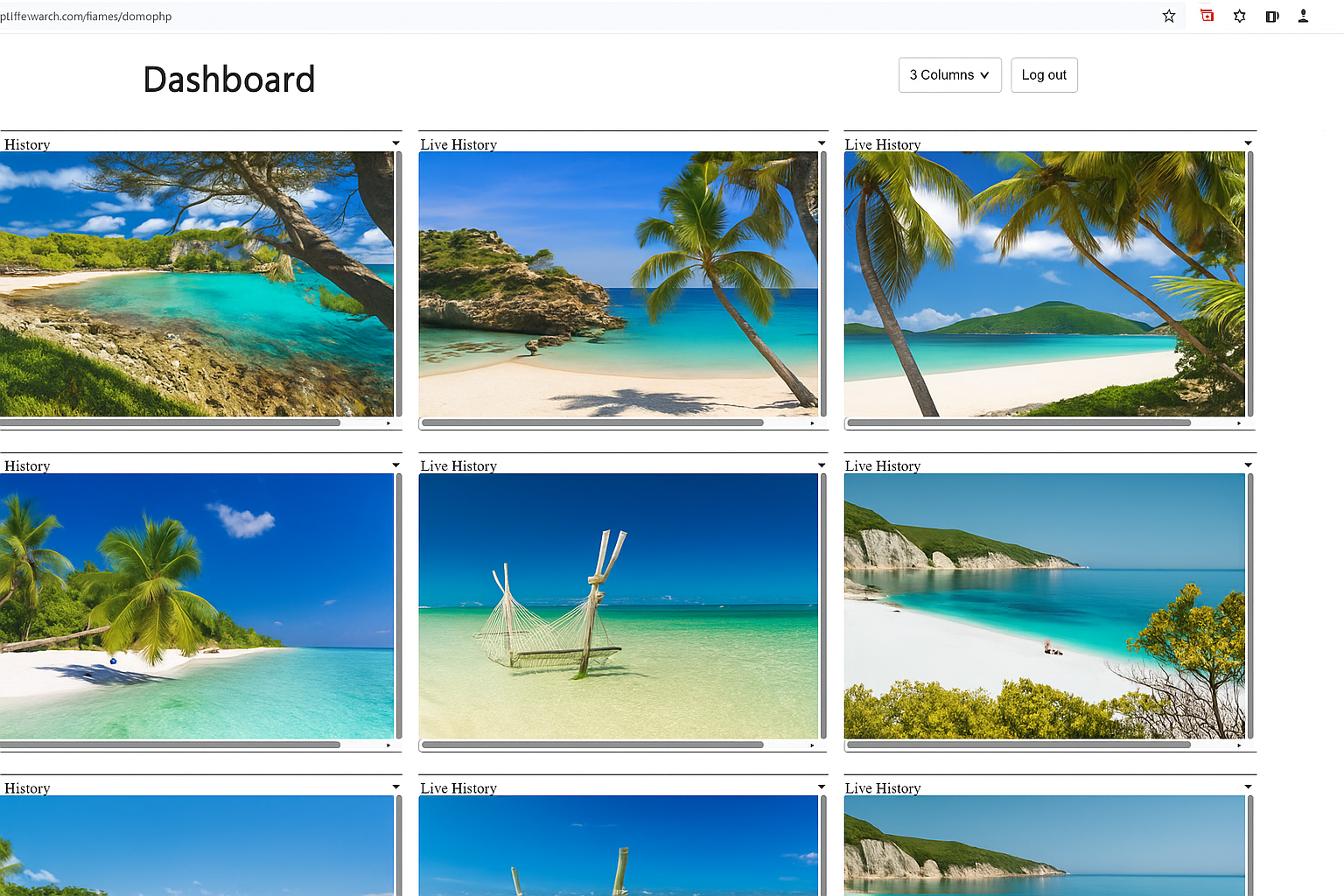
Illustrative Wolfeye dashboard with several company-controlled PCs. Any real monitoring must comply with applicable laws, contracts and internal policies.
Timesheets may say “8 hours”, but many business owners and team leads still ask: What actually happened during those hours?
This is especially common with remote staff, freelancers, agencies and project-based work where output is harder to observe day-to-day. Sometimes it is intentional “time theft”. Often it is simply unclear expectations, context switching, or wasted time that nobody notices early.
Tools like Wolfeye Remote Screen can technically help by providing live screen view (and, if enabled, screenshot history) on company-controlled Windows PCs. This can add a practical layer of visual verification when you need clarity on how time is spent.
Important legal disclaimer: Screen monitoring is legally sensitive. Whether you may use monitoring software at all, for which purposes (for example, training supervision, quality assurance or security), and under which conditions (for example, user information, consent, internal policy, contractual clauses) depends on the laws in each relevant country and your specific setup.
This article is not legal advice. It describes technical possibilities and typical organisational patterns only. Before you deploy Wolfeye or any monitoring tool, always obtain independent legal advice in all relevant jurisdictions and ensure your policies and information duties are met.
1. Why Timesheets Drift Away from Reality (Especially Remote & Project Work)
Timesheets can become unreliable for several reasons:
- Low visibility: in remote teams, managers don’t see day-to-day screen-level reality.
- Output delays: in project work, results appear days later, making it hard to connect time → progress.
- Context switching: people jump between tools, chats and tasks; “busy” does not always mean “productive”.
- Misaligned expectations: what managers consider “work time” may differ from how contractors interpret it.
- Intentional abuse: inflated hours or “fake timesheets” in the worst cases.
For many SMBs, the goal is not constant surveillance. It’s having a reliable way to verify work when something doesn’t add up — and to improve workflows and expectations early.
2. What Live Screen View + Screenshot History Can Do for Timesheet Verification
Live screen monitoring is a visual verification layer. Used responsibly and legally, it can help you:
- Validate suspicious patterns quickly (for example: hours billed with little visible work progress).
- Understand where time goes (tools, workflows, waiting times, repetitive steps).
- Support coaching and training by seeing where someone gets stuck on-screen.
- Document work blocks with optional screenshot history (retention should be defined with legal/compliance guidance).
What it is not:
- It is not a replacement for clear deliverables, project management and agreed KPIs.
- It is not a “permission” to monitor. Legality depends on country, use case and required user information/consent.

Example: Wolfeye dashboard with multiple company-controlled PCs. Technical illustration only. Any real monitoring must comply with applicable laws, contracts and internal policies, and may require prior user information/consent depending on country and use case.
3. Typical “Wasted Time” Patterns You Can Recognise (Without Guessing)
If a timesheet looks inflated, the underlying reason is often visible on-screen. Common patterns include:
3.1 Long idle or distraction blocks
- extended non-work browsing during billed hours,
- frequent “micro-breaks” that add up to hours,
- workday dominated by entertainment/social feeds instead of tools.
3.2 “Busywork” that does not move the project forward
- reformatting and minor edits without delivering milestones,
- repetitive manual steps that should be automated,
- spending most time searching for information due to missing SOPs.
3.3 Workflow friction (often not malicious)
- waiting for access, approvals, credentials, or broken tooling,
- unclear requirements leading to rework,
- constant switching between chats, email and tasks without focus blocks.
These signals are not automatically “misconduct”. They can be a basis for process improvement, training and better project scoping — within legal limits and transparent rules.
4. How Wolfeye Works Technically (Company PCs)
From a technical perspective, Wolfeye Remote Screen follows a simple model:
- Install a small agent on each company-controlled Windows PC you want in scope.
- Those PCs appear in your Wolfeye dashboard in a live grid view.
- Authorised users can open a single PC in a large live view.
- Optionally, you can enable screenshot history to review the day in intervals (retention should be defined with legal/compliance counsel).
A practical timesheet-verification setup usually focuses on:
- project-critical PCs (billing-heavy roles),
- new hires during onboarding/training,
- teams where deliverables are hard to evaluate quickly.
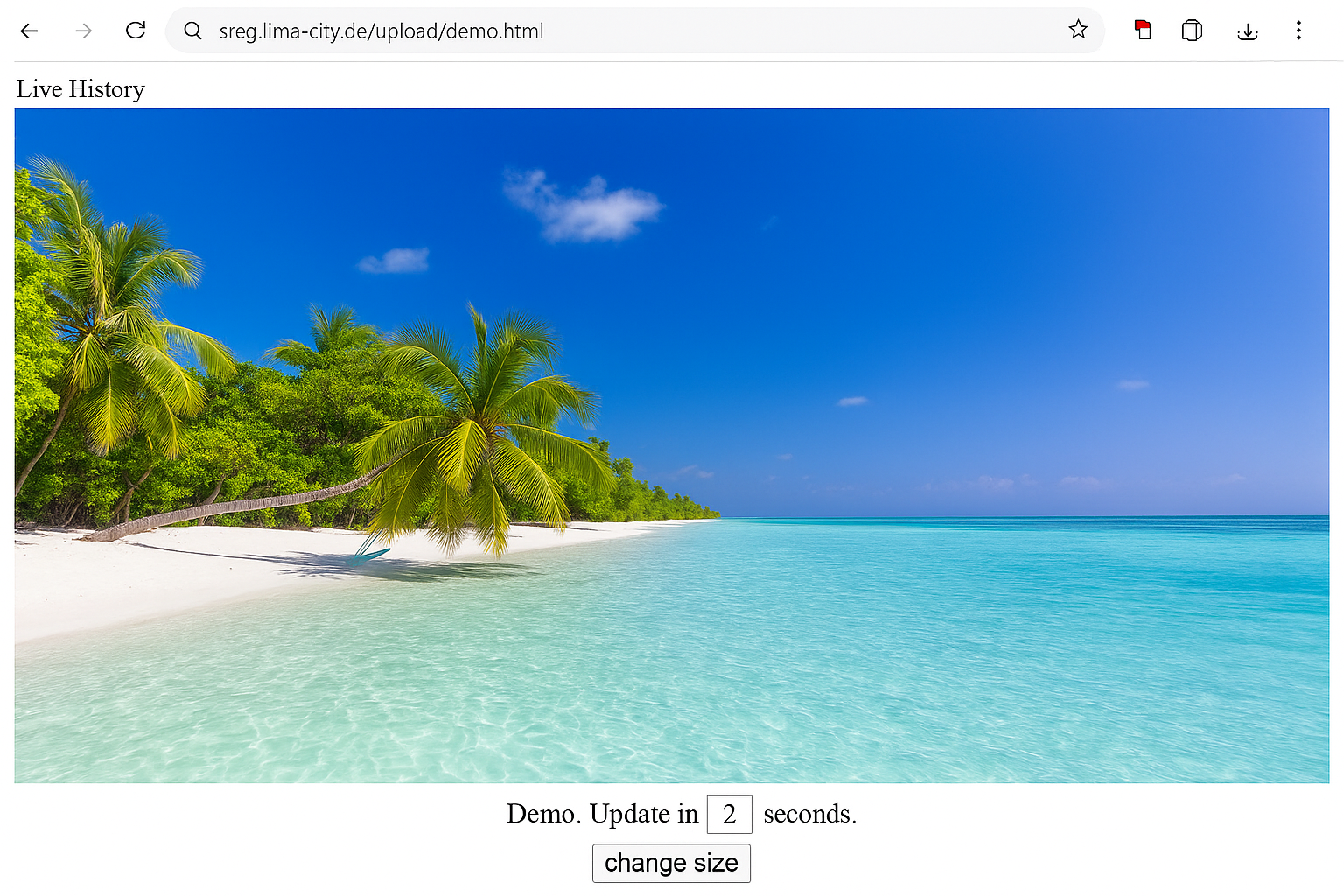
Example: single live screen view of a company-controlled PC. Whether and how you may use monitoring depends on applicable laws, contracts, internal policies and user information/consent requirements.
5. A Responsible Workflow: Verify → Clarify → Improve (Instead of Constant Watching)
To keep monitoring legally and culturally safer, many organisations use a lightweight workflow:
5.1 Verify (trigger-based checks)
Use live view when there is a reason: inconsistent timesheets, missed deadlines, quality issues, or onboarding supervision (where legally permitted).
5.2 Clarify (talk to the person)
Often you will discover non-malicious causes: unclear requirements, broken access, missing SOPs, or the need for training.
5.3 Improve (fix the system)
Use what you learn to tighten deliverables, improve SOPs, reduce friction, and align timesheet rules. Monitoring should not replace good management — it should help you find the real bottleneck.
5.4 Document (only if configured and justified)
If screenshot history is enabled, define retention and access strictly. This is a legal/compliance decision — not just a technical setting.
6. Legal & Policy Disclaimer (Read This Before Using Any Monitoring)
This article describes technical possibilities and typical organisational patterns only. It is not legal advice.
Whether you may use live screen monitoring and screenshot history depends on:
- the laws and regulations in each relevant country,
- your specific use case (for example, training supervision, quality assurance, security investigations),
- whether users must be informed and/or provide consent,
- employment agreements, client contracts and internal policies.
Before using Wolfeye or any monitoring tool, obtain qualified legal advice in all relevant jurisdictions. Restrict dashboard access to authorised roles, document the purpose and scope, and apply data minimisation (only what you actually need).
7. Video: Time Theft & Fake Timesheets — Verifying Real Work with Live Screen View
The following video shows a technical demo of how live screen view and screenshot history can help validate how time is spent on company-controlled PCs.
Important: The video is for technical illustration only and does not replace legal advice. Always ensure monitoring is lawful in your country and for your use case, and inform users where required.
Video: “Time Theft & Fake Timesheets — How to Verify Real Work with Live Screen View”. Technical demo only; no legal advice.
Frequently Asked Questions – Timesheet Verification
No. Wolfeye provides visual screen visibility (live view and optional screenshot history). It can support timesheet verification, but it does not replace time tracking systems, project management, contracts or clear deliverables.
Technically, it works on PCs where the agent is installed. In practice, most organisations use it on company-controlled PCs. Using monitoring on private devices is a complex legal and contractual topic — obtain legal advice first.
In most organisations, no. A trigger-based approach (spot checks or onboarding supervision) is often more acceptable and reduces legal and cultural risk — where legally permitted.
This depends on laws, your use case and policies. Define retention and deletion with legal/compliance counsel. Keep it limited, purpose-based and access-restricted.
Conclusion
Timesheet problems are often a visibility problem — not just a “people problem”.
Used responsibly and where lawful, live screen view can help you:
- verify questionable timesheets with fast visual context,
- discover non-obvious bottlenecks and workflow friction,
- improve training, SOPs and project scoping in remote teams.
Want to see what timesheet verification could look like in your own live dashboard (company PCs)?
Start 14-Day Free Trial
Wolfeye is monitoring software for company-controlled PCs. Any use must comply with the laws and regulations that apply in all relevant countries, your industry and your specific use case (for example, training supervision, quality assurance or security). In many jurisdictions, monitoring may require prior user information, explicit consent, contractual clauses and additional compliance measures. This article and the embedded video are for general technical and organisational information only and do not constitute legal advice or a guarantee of legal admissibility.
Before using any monitoring software such as Wolfeye, always obtain independent legal advice in all relevant countries about whether and how you may monitor company-controlled PCs (for example in training, quality assurance or security scenarios) and under which conditions users must be informed or give consent.