Insider Threats & Data Leaks: How Live Screen Monitoring Helps Detect Risky Behavior Early
A practical security-focused guide for SMBs and IT service providers: how live screen view plus screenshot history can support early detection and documentation of risky activity on company-controlled PCs — only where legally permitted. No legal advice.
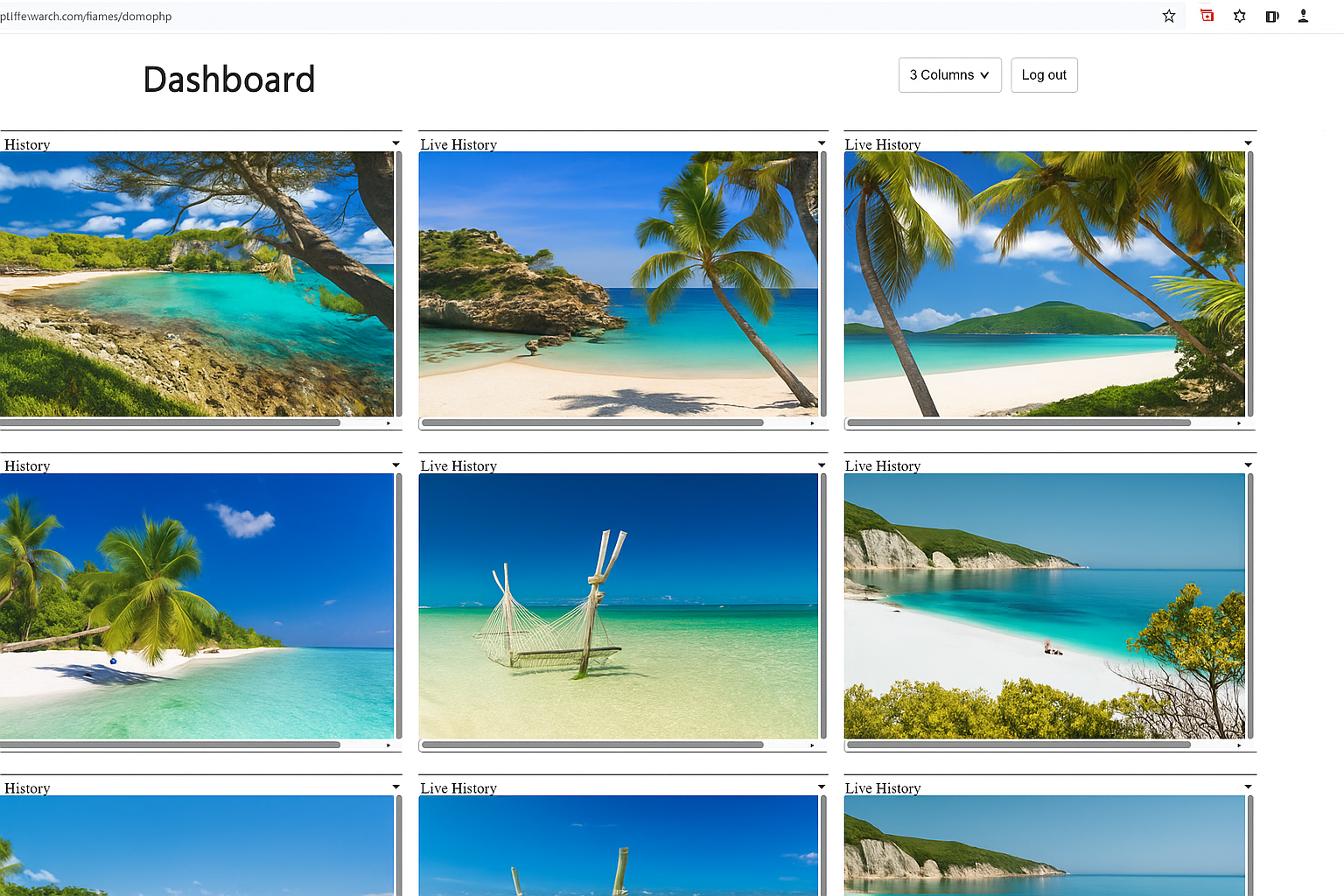
Illustrative Wolfeye dashboard with several company-controlled PCs. Any real use of monitoring must comply with applicable laws, contracts and internal policies.
The biggest security risks do not always come from external hackers. In many SMB incidents, the first “signal” is something visible on a screen: unusual file transfers, sensitive records opened at odd times, personal cloud uploads, or data copied into places it should never go.
This is where live screen monitoring (and optionally screenshot history) can be useful — not as a replacement for security tooling like EDR, access control, logging or DLP, but as an additional layer of visual confirmation when something looks suspicious.
Typical questions from business owners and IT providers include:
- “How can we detect risky on-screen behavior before a data leak becomes a crisis?”
- “Can we document what happened on a company PC in a simple way?”
- “Is there a lightweight approach for SMBs without a full SOC?”
Important: Monitoring employees and screens is legally sensitive. Whether you may use monitoring software at all, for which purposes (for example, training supervision, quality assurance, or security), and under which conditions (for example, user information, consent, internal policy, contractual clauses) depends on the laws and regulations in each relevant country and on your specific setup.
This article is not legal advice. It describes technical possibilities and common organisational patterns only. Before using Wolfeye or any monitoring tool, always obtain qualified legal advice in all relevant jurisdictions and ensure you follow your internal policies, employment agreements, and information requirements.
1. Why “Insider Threats” and “Data Leaks” Are Hard for SMBs
SMBs typically do not have a full-time security operations team. Yet they still handle:
- customer data, invoices, contracts, and payment information,
- intellectual property (offers, pricing, product plans),
- access credentials to cloud systems, CRMs, ticketing tools, and shared drives.
Common insider-risk scenarios (examples) are:
- malicious intent (a disgruntled employee, intentional leakage),
- carelessness (sending the wrong attachment, uploading sensitive files to a personal cloud),
- compromised accounts (an attacker uses an internal account, but the “actions” happen on a user’s screen).
For many SMBs, the challenge is not “collecting data” — it is knowing what to look at, when, and how to react without turning the company into a surveillance culture. A security-oriented approach focuses on:
- company-controlled devices,
- limited, purpose-based monitoring (for example, security investigations, training, quality assurance),
- restricted access (only authorised roles),
- clear documentation and legal review.
2. What Live Screen Monitoring Can (and Cannot) Do for Leak Prevention
Live screen monitoring is a visual layer. It can help you:
- spot unusual behavior early when a risk indicator appears (for example, a staff member suddenly moving lots of sensitive files),
- confirm context (is this legitimate work, training, or something that violates policy?),
- document what happened (with screenshot history where enabled) to support internal incident handling.
It cannot replace core security controls. For strong security you still need (examples):
- least-privilege access, MFA, and proper account lifecycle management,
- endpoint protection/EDR, patching, backups,
- logging and audit trails in your cloud systems,
- data classification and (where appropriate) DLP policies.
Think of Wolfeye as a fast, practical visibility tool for company PCs: you see what is actually happening on screens and can quickly validate concerns — only where permitted by law and your internal rules.

Example: a single dashboard showing multiple company-controlled PCs. This is technical illustration only. Any real monitoring must comply with applicable laws, contracts, and internal policies, and may require prior user information and consent depending on country and use case.
3. Practical Early-Warning Signals You Can Spot on Screens (Security Use Case)
In insider-risk and leak-prevention work, the goal is not “watching employees” — it is recognising high-risk patterns early enough to prevent damage. Depending on your environment, typical on-screen signals may include:
3.1 Unusual data movement patterns
- large exports from CRM/ERP systems that are not typical for the role,
- mass copying of files between folders or drives,
- bulk renaming, archiving, or compressing sensitive folders.
3.2 Transfers to unapproved destinations
- uploads to personal cloud storage accounts,
- webmail usage for sending work files outside approved channels,
- file-sharing links created outside your approved toolset.
3.3 “Policy mismatch” moments
- accessing confidential data without a clear operational reason,
- opening internal admin consoles or credential vaults without authorisation,
- repeated attempts to bypass restrictions (for example, trying different tools for the same prohibited action).
These are not proof of wrongdoing — they are signals that may justify a closer look under your security policy and within legal limits. In a well-governed setup, you define:
- which device groups are in scope,
- which triggers justify live review,
- who may access the dashboard,
- how long screenshots (if enabled) are retained.
4. How Wolfeye Supports Security Investigations on Company PCs (Technical Overview)
From a technical perspective, Wolfeye Remote Screen follows a simple model:
- Install a small agent on each company-controlled Windows PC that is in scope.
- Those PCs appear in your Wolfeye dashboard in a grid view.
- Authorised users can open a single PC in a larger live view.
- Optionally, you can enable screenshot history to review what happened across the day (use retention limits defined with your legal/compliance teams).
For insider-risk prevention, a common approach is to monitor high-risk endpoints first, for example:
- finance PCs that handle payments and invoices,
- sales ops PCs with CRM exports,
- support PCs that access many customer accounts,
- shared workstations in back office environments.
Always keep the governance piece in mind: even if something is technically possible, you must only use it where you are allowed — based on your country, your use case, and your information/consent obligations.
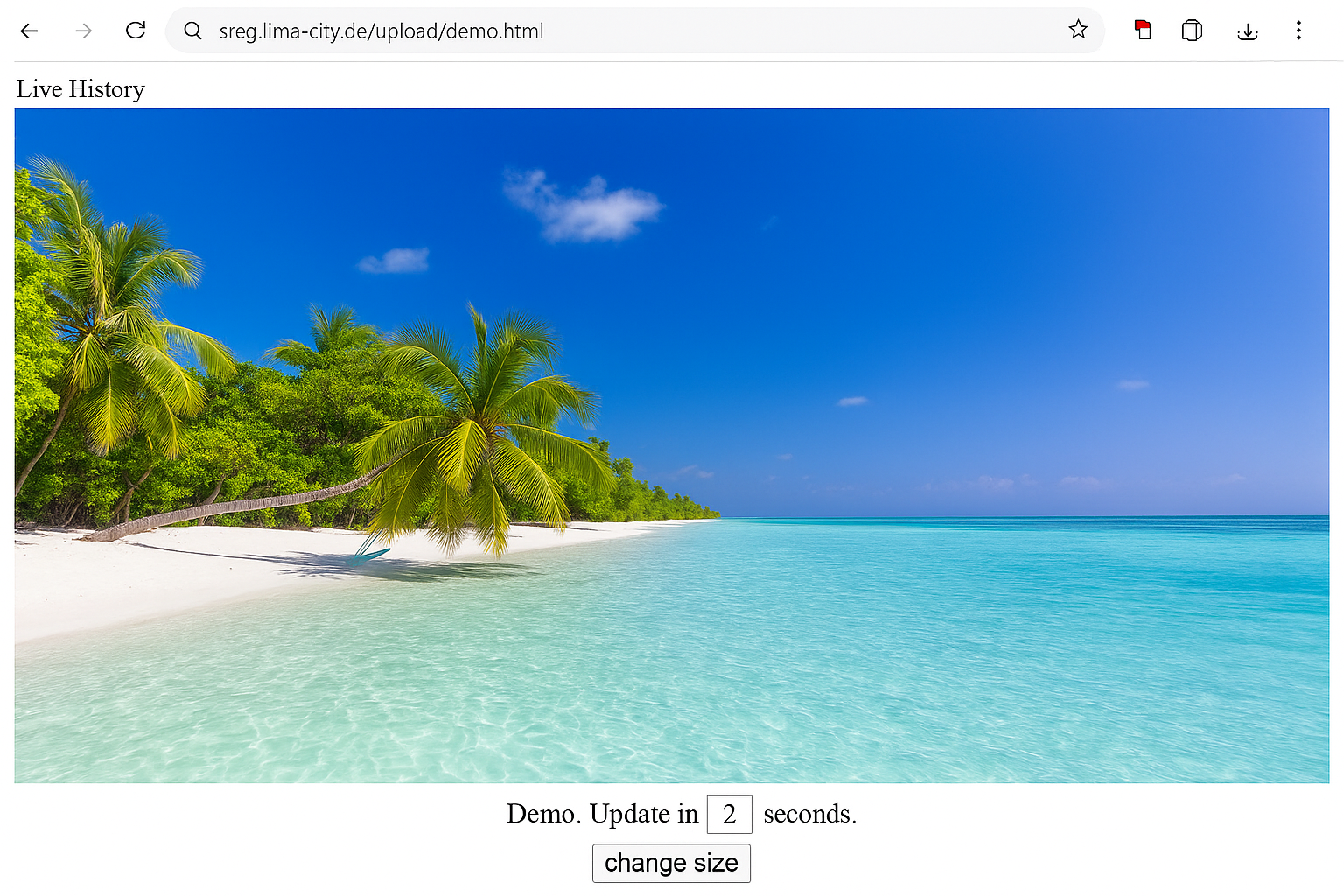
Example: a single live screen view of a company-controlled PC. This shows a technical capability only. Whether and how you may use such monitoring depends on applicable laws, contracts, internal policies, and user information/consent requirements.
5. A Simple SMB Workflow: Detect → Validate → Document → Respond
Many SMBs and IT providers use a lightweight workflow that avoids “continuous monitoring” while still improving security response:
5.1 Detect (trigger-based)
Triggers can be operational (for example, a client reports unusual emails) or technical (for example, a suspicious alert in your endpoint protection). The trigger justifies a time-limited review — where legally allowed.
5.2 Validate (short live check)
A short live view can clarify context quickly: is the action legitimate, a mistake, or a clear policy violation? This prevents overreacting based on rumours or incomplete logs.
5.3 Document (if screenshot history is enabled)
If you enable screenshot history, it can support internal incident documentation — for example, to understand the sequence of actions. Retention and access must be defined with legal/compliance counsel.
5.4 Respond (with IT + management)
Response should follow your internal incident process: limit access, isolate affected systems where appropriate, rotate credentials, and involve the right stakeholders (IT/security, management, HR, legal counsel). This article does not provide legal advice on how to handle employment issues or investigations.
6. Legal & Policy Disclaimer (Read This Before Using Any Monitoring)
This article describes technical possibilities and organisational patterns only. It is not legal advice.
Whether you may use live screen monitoring and screenshot history depends on:
- the laws and regulations in each relevant country,
- your specific use case (for example, security investigations, training supervision, quality assurance),
- whether users must be informed and/or provide consent,
- employment agreements, client contracts, and internal policies.
Before using Wolfeye or any monitoring tool, obtain qualified legal advice in all relevant jurisdictions. Do not deploy monitoring “by default”. Restrict access to authorised roles and document the purpose and scope of use.
7. Video: Insider Threats & Data Leaks — How Live Screen Monitoring Protects Your Company
The following video shows a technical demo of how live screen view and screenshot history can support insider-risk prevention on company-controlled PCs.
Important: The video is for technical illustration only and does not replace legal advice. Always ensure you are allowed to use monitoring software in your country and for your specific use case, and inform users where required.
Video: “Insider Threats & Data Leaks — How Live Screen Monitoring Protects Your Company”. Technical demo only; no legal advice.
Frequently Asked Questions – Insider Threats & Data Leaks
No. Wolfeye provides visual screen visibility (live view and optional screenshot history). It complements security controls but does not replace DLP, EDR, access control, audit logs, or incident response procedures.
That is the recommended organisational approach. Restrict dashboard access to defined roles (for example, owner, security lead, trusted IT provider) and document who is allowed to view which device groups and for what purpose.
Technically yes, as long as the PCs are company-controlled Windows devices with the agent installed and connected. Whether you may monitor shared workstations depends on local law and your policies — get legal advice.
This is not just a technical question. Retention should be defined with legal/compliance advice based on your country, your use case, and your internal rules. Keep retention limited and purpose-based.
Conclusion
Insider threats and data leaks are often visible on screens before they become a full incident.
From a technical and organisational perspective, live screen monitoring can help SMBs and IT providers to:
- validate suspicious signals quickly with a short live review,
- understand context and reduce false alarms,
- document sequences of actions with screenshot history (where enabled and properly governed).
A pragmatic approach is: define the scope (company PCs only), define triggers (not constant watching), restrict access, obtain legal advice, and then run a focused pilot for security visibility on high-risk endpoints.
Want to see how a security-focused live screen dashboard could work for your company PCs?
Start 14-Day Free Trial
Wolfeye is monitoring software for company-controlled PCs. Any use must comply with the laws and regulations that apply in all relevant countries, your industry and your specific use case (for example, training supervision, quality assurance or security investigations). In many jurisdictions, monitoring may require prior user information, explicit consent, contractual clauses and additional compliance measures. This article and the embedded video are for general technical and organisational information only and do not constitute legal advice or a guarantee of legal admissibility.
Before using any monitoring software such as Wolfeye, always obtain independent legal advice in all relevant countries about whether and how you may monitor company-controlled PCs (for example in training, quality assurance or security scenarios) and under which conditions users must be informed or give consent.