How to View Employee Screens Discreetly on Company PCs (Full Technical Walkthrough)
A practical, non-legal guide for SMBs and IT service providers: how live screen viewing works technically on company-owned Windows PCs — from installation to your first live screens in the dashboard — and why you must clarify legal rules in your country before using any monitoring software.
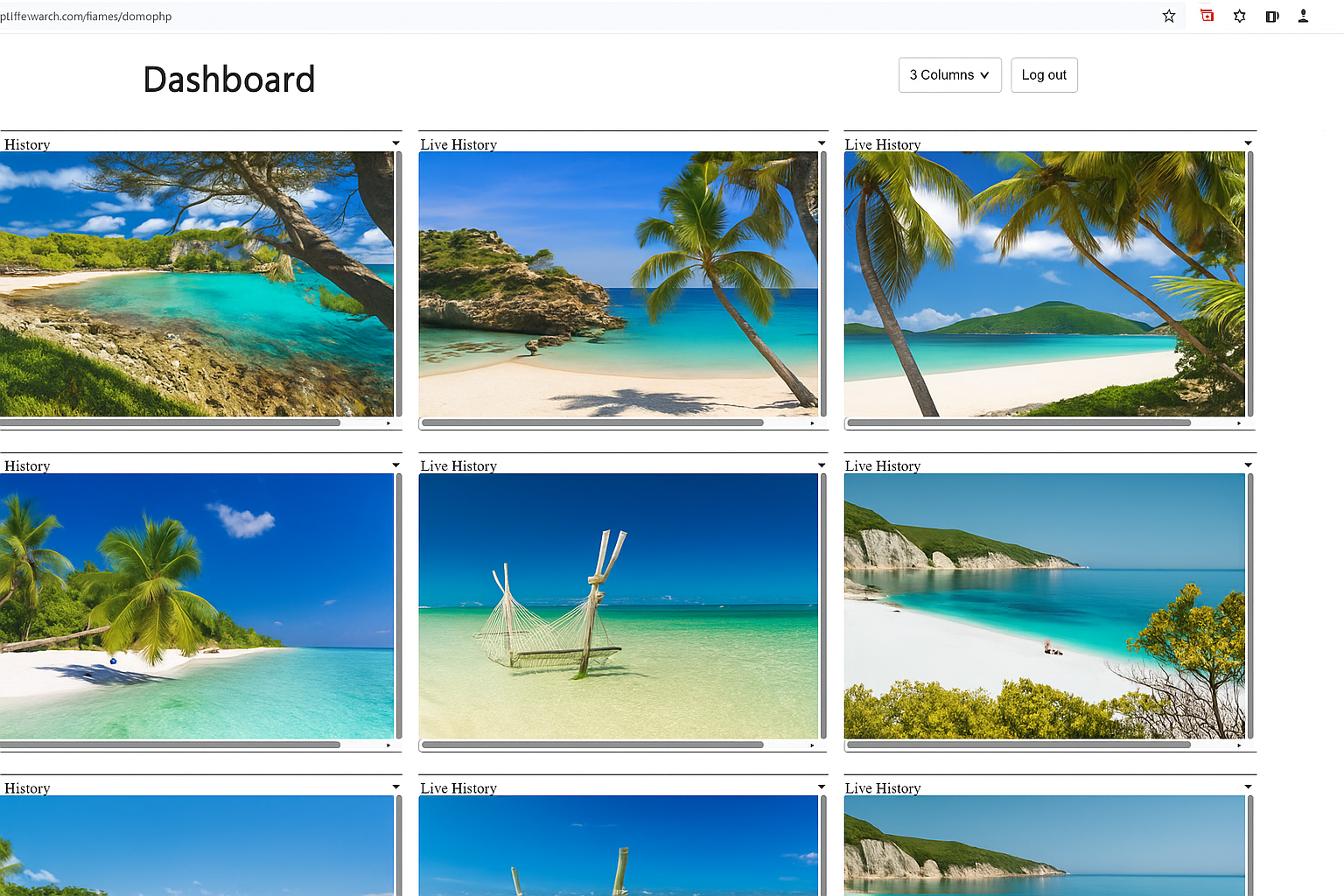
Illustrative Wolfeye dashboard with several company-owned PCs. Any real monitoring use must comply with applicable laws, contracts and internal policies.
Many business owners and IT providers look for a way to get real-time visibility into what happens on selected company-owned Windows PCs — for example during onboarding, training, quality supervision, or security investigations.
Typical questions sound like:
- “Is it technically possible to view employee screens live from one dashboard?”
- “Can we set up discreet live screen viewing on company PCs without disrupting work?”
- “How do we go from zero to first live screens — step by step?”
Important: This article is not legal advice. Employee monitoring rules vary widely by country, industry, contracts, and specific use case. In many jurisdictions, whether and how you may use monitoring software depends on requirements such as prior notice, internal policies, consent, employment law, and data protection rules. Before using Wolfeye (or any monitoring software), obtain legal advice in every relevant jurisdiction.
With that clear limitation in mind, the rest of this guide focuses purely on the technical and organisational side: what discreet live screen viewing means technically, what you need, and how to set it up in practice.
1. What “Discreet Live Screen Viewing” Means Technically
In a purely technical context, “discreet” live screen viewing usually means:
- The software runs in the background on company-owned Windows PCs.
- There are no constant pop-ups or interruptions during normal work.
- Authorised viewers can open a live dashboard to see multiple screens at once (grid view).
- You can open one specific PC screen in a larger view when you need detail.
- Optionally, you can enable a screenshot history on selected PCs to review past activity (for example, periodic screenshots).
Technically, Wolfeye follows a simple model:
- Agent on the PC: a small software component is installed on each company PC you want to view.
- Dashboard access: you log in to your Wolfeye dashboard and see those PCs.
- Live view + history (optional): live viewing is immediate; screenshot history can be enabled per PC depending on your setup.
Discreet does not mean “rule-free.” It only describes how the software behaves technically on the device. Whether you may use it, for which purposes, and under which transparency or consent requirements is a legal and policy question you must clarify separately.
2. What You Need Before You Start (Company PCs, Access, and Basic Setup)
To get reliable live screen viewing, most organisations start with a clean, controlled setup:
- Company-owned Windows PCs: Wolfeye is designed for company-controlled devices (office PCs, company laptops, training room PCs).
- Admin rights for installation: you need permission to install software on the target devices.
- Stable internet access: the PCs must be able to reach your Wolfeye account to send screen content.
- Clear internal roles: decide who is allowed to view screens (owner, team lead, supervisor, IT provider) and why.
- A defined use case: keep it specific (examples: training supervision, quality checks, security). This is important both operationally and for legal review.
If you are an IT provider or MSP, it also helps to define how you group and label devices (by client, location, team, or project) so the dashboard stays readable once you scale from 5 to 50+ PCs.

Example: a Wolfeye dashboard showing multiple company-owned PCs side by side. Image for technical illustration only. Any real monitoring use must comply with applicable laws, contracts, and internal policies.
3. Full Technical Walkthrough (From Zero → Your First Live Screens)
This section is a practical “do this, then that” walkthrough — the same sequence most SMBs and IT providers follow when they want to see their first live screens quickly on company-owned PCs.
3.1 Step 1: Get your dashboard access (account + demo if needed)
Start by creating your Wolfeye account and accessing your dashboard. Many teams begin with a short live demo, because it lets you:
- see how the dashboard looks in real usage,
- understand grid view vs. single-screen view,
- confirm the workflow before rolling out to multiple PCs.
After signup, you will have a dashboard link and login credentials. That dashboard is where your monitored PCs will appear once the agent is installed and connected.
3.2 Step 2: Install the Wolfeye agent on a first company PC
To view a PC screen live, Wolfeye must be installed on that specific company PC. A typical pilot approach is:
- Pick one company PC for a first test (for example a training PC or a supervisor’s own device).
- Download the installer from your Wolfeye setup area.
- Run the setup wizard and complete installation.
After installation, Wolfeye provides a small control window on the PC. In normal setups, the final connection consists of two simple actions:
- Share Screen — to start sending screen content to your dashboard.
- Stealth Mode — to run unobtrusively in the background (where permitted by your rules and local laws).
In the demo workflow shown in the video, the installation folder is created under a public documents path (for example: C:\Users\Public\Public Documents\...). The exact internal file names are not important for daily use — what matters is that the PC is connected and shows up in your dashboard.
3.3 Step 3: Verify the first live screen in the dashboard
Once the agent is installed and screen sharing is enabled on that PC, go back to your dashboard:
- You should now see the first PC tile appear in the grid.
- The tile updates with the live screen content.
- You can switch the grid layout (for example, 2 columns for bigger screens or 3 columns for more devices) depending on how many PCs you view.
3.4 Step 4: Open one screen in a large view (for detail)
When you need to focus on a single device (for example during onboarding or when investigating a specific incident), you can open that PC in a dedicated view:
- Right-click the PC tile and open it in a new tab (or use the dashboard option to open the single screen view).
- Now you see that one screen much larger — useful for details, not just overview.
3.5 Step 5 (Optional): Enable screenshot history on selected PCs
If you need to review what happened earlier (instead of only seeing live), you can enable screenshot history on specific PCs. In the demo workflow, screenshots are captured periodically (for example, every 5 minutes) and can be reviewed as a timeline.
Operational tip: Many companies enable screenshot history only for specific, high-risk or training-related PCs — and keep general live viewing as the primary mode for day-to-day supervision.
3.6 Step 6: Scale from 1 PC to a team rollout
After the first PC works, scaling is mostly repetition plus organisation:
- Install the agent on the next set of company PCs (for example, onboarding laptops, support PCs, training room PCs).
- Group devices logically (by team, location, or client if you are an MSP).
- Limit dashboard access to authorised users only and document the purpose internally.
In SMB environments this can be done manually device-by-device. In IT provider environments, rollouts are often done via remote software distribution or RMM — always within the limits of your contracts and local laws.
4. How Teams Use Live Screen Viewing in Practice (Without Disrupting Work)
Once you have your devices connected, most organisations use live screen viewing in short, practical routines — not as permanent “all-day watching.” Common patterns include:
4.1 Onboarding and probation periods
During the first days or weeks, managers and trainers can quickly see whether new staff follow the right steps in CRM, ERP, ticketing, or internal tools. This often reduces back-and-forth because you immediately see where someone is stuck.
4.2 Quality supervision for service teams
Support desks, call centers, and back-office teams often use a grid overview to verify that workflows are followed and that the right systems are used — especially during peak times or when quality complaints occur.
4.3 Security and insider-risk awareness (technical visibility)
In security-sensitive environments, a live view can provide fast technical visibility during an incident response process — for example when suspicious activity is reported on a specific company PC. The key is to have clear internal rules about who may view screens and for which purpose.
4.4 IT providers and MSPs: multi-client supervision (where agreed)
IT providers who manage multiple client environments can use Wolfeye (where contractually agreed and legally permitted) to supervise key PCs at client sites, especially for training setups, outsourced teams, or high-risk workstations.
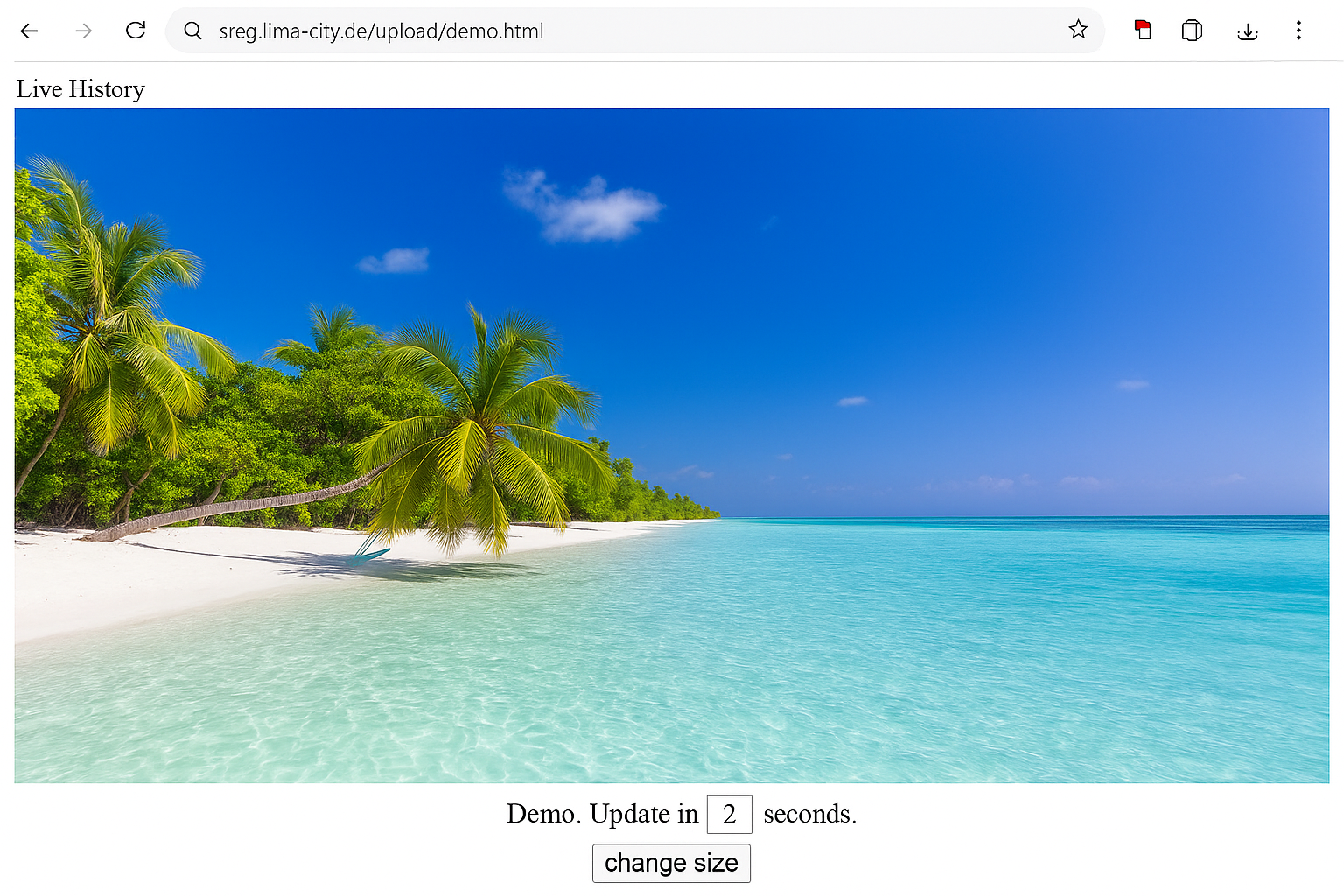
Example: single-screen live view of one company PC. It shows what is technically possible; it does not determine what is legally permitted. Always get legal advice for your country and use case.
5. Operational Best Practices (Non-Legal) for Discreet Live Screen Monitoring
To keep live monitoring useful (and not chaotic), SMBs and IT providers typically implement a few operational best practices:
- Start with a pilot: connect 1–3 PCs first (training or onboarding devices), then scale to a team.
- Use clear naming and grouping: name devices by team/location (“Support-01”, “Training-Laptop-02”) and group them so the dashboard stays readable.
- Limit access: restrict dashboard logins to a small set of authorised people and keep credentials secure.
- Use short review routines: quick grid checks at key moments often deliver more value than constant viewing.
- Use screenshot history selectively: enable it for defined scenarios (training, quality reviews, investigations) rather than everywhere by default.
- Document internal purpose: write down why you use live viewing (training, quality, security), because it keeps implementation disciplined and supports legal review.
These are operational patterns only — not legal guidance. Always validate your monitoring approach with qualified legal counsel in all relevant jurisdictions.
6. Explicit Non-Legal Disclaimer (Please Read)
This article and the embedded video describe technical features and common organisational usage patterns for Wolfeye Remote Screen on company-owned Windows PCs. They are provided for general information only and do not constitute legal advice.
Monitoring employees or contractors can be regulated by employment law, privacy/data protection rules, works councils, contractual obligations, industry rules, and local policies. Requirements differ widely by country and scenario. In many jurisdictions, lawful use can depend on factors such as:
- the specific purpose (for example, training supervision, quality assurance, security),
- whether devices are company-owned and company-controlled,
- whether you must provide prior notice or obtain consent,
- how access is restricted and how long any data (for example, screenshots) is retained.
Before deploying Wolfeye or any monitoring software, obtain independent legal advice in all relevant countries and confirm that your planned use case is allowed and implemented correctly.
7. Video: Full Technical Walkthrough (Installation → Live Dashboard → Stealth Mode)
The following video shows a technical walkthrough of how live screen viewing works on company-owned PCs — including the dashboard grid view, single-screen view, and optional screenshot history.
Reminder: The video is not legal advice. Always confirm with legal counsel whether and how monitoring is permitted in your country and use case, and what information/consent requirements apply.
Video: “How to Secretly View Employee Screens on Company PCs – Full Technical Walkthrough”. Technical illustration only. Always obtain legal advice before using monitoring software.
Frequently Asked Questions – Discreet Live Screen Viewing on Company PCs
No. Wolfeye is not a remote desktop session in the classic sense. Technically, it sends screen content to your dashboard over the internet, so you can view live screens without logging into each PC via RDP.
Yes. The main dashboard is designed as a grid so you can see several company PCs side by side. You can also open one PC in a larger single-screen view when you need more detail.
Screenshot history can be enabled per PC (depending on configuration). In the demo workflow, periodic screenshots (for example every few minutes) can be reviewed to understand past on-screen activity. Define retention and access rules with legal counsel.
In practice, IT providers and MSPs often supervise multiple device groups. The key is to keep client environments clearly separated contractually and operationally, and to ensure monitoring is permitted and agreed for each client.
Conclusion
Discreet live screen viewing is a technical capability — not an automatic permission.
From a technical and operational standpoint, Wolfeye Remote Screen can help SMBs and IT providers:
- connect selected company-owned PCs to one dashboard,
- see live screens in grid view (and open one screen in detail),
- optionally review screenshot history for defined scenarios.
Want to see your own company PCs in a live Wolfeye dashboard?
Start 14-Day Free Trial
Wolfeye is monitoring software for company-owned PCs. Any use must comply with the laws and regulations that apply in all relevant countries, your industry, and your specific use case (for example, training supervision, quality assurance, or security). In many jurisdictions, lawful use depends on factors such as prior notice, consent, internal policies, data protection rules, and contractual terms. This article and the embedded video are for general technical and organisational information only and do not constitute legal advice or a guarantee of legal admissibility.
Before using any monitoring software such as Wolfeye, always obtain independent legal advice in all relevant countries about whether and how you may monitor company-owned PCs and under which conditions users must be informed or give consent.